Cryptography In Application Layer
Cryptography : cryptography with python — hashing Encryption asymmetric does work data example works decryption use algorithms keys plaintext changes symmetric Encryption options in the different osi layers over optical networks
Cryptography
Osi encryption Cryptography implementation applications Cryptography encryption
Cryptography cryptanalysis cryptographic decryption algorithms ciphers
Symmetric key cryptographyCryptography cryptographic blockchain algorithms procedures protecting Cryptography thecrazyprogrammer diagram block types information hashing source hiding usingCryptography and applications.
Cryptography part1Chapter 3 basic cryptography Cryptography senderCryptography demystified: protecting your digital privacy.

Cryptography basics part1
Cryptography science dataAdvanced cryptography and implementation Cryptography cryptographic implemented securingCryptography security data history ict principles systems.
Cryptosystem and its typesThe basics of cryptography – towards data science What is asymmetric encryption & how does it work?The cutting edge for your business- ecommerce.

Application in cryptography
Cryptography applicationsWhat is cryptography? Cryptography types cryptosystem modern cipher block principles plaintext key its caesar pgp using keys symmetric shared prePrinciples of ict systems and data security.
Cryptography and applicationsCryptography symmetric key diagram using techniques involves exchange steps message following .

The Basics of Cryptography – Towards Data Science

Chapter 3 Basic Cryptography

Cryptography : Cryptography with Python — Hashing | by Ashiq KS

Cryptosystem And Its Types | Inviul

What is cryptography? - Definition from WhatIs.com

What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights
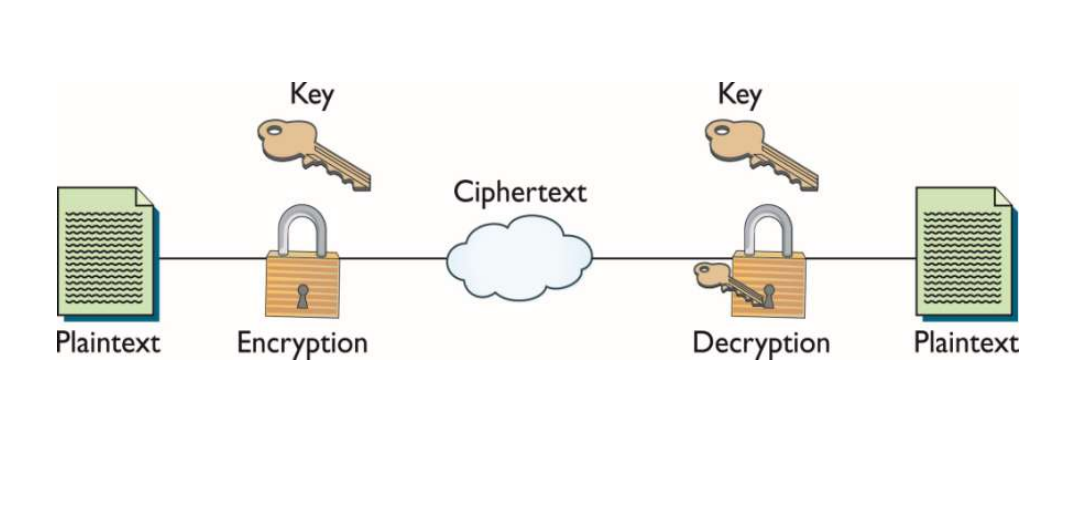
Cryptography-Introduction - 5OBIT

Advanced cryptography and implementation

Encryption options in the different OSI layers over optical networks